We publish rigorous academic articles, policy reports with evidence-based recommendations, and accessible blog posts for broader audiences.

This brief goes beyond the widespread use of “inclusion” as a guiding principle for digital identity systems, particularly in relation to stateless people and those at risk of statelessness. While expanding access to identification is often seen as a pathway to rights and services, the report highlights that inclusion alone is not enough. For people whose nationality is unrecognized or in doubt, being added to an identity system may not improve their legal status—and, in some cases, may entrench existing forms of exclusion.

From the Alps to the Himalayas to the Lesotho Highlands, small states are showing what it means to exercise agency in a system tilted against them. Their experiments, technical, political, and ethical, hold lessons not just for themselves, but for everyone seeking to build a more just and plural digital world.

Humanitarian aid is becoming increasingly budget-constrained, privatised, and technocratic, while also facing outright bans, forced withdrawals, and threats to its very existence. We argue organisations need to invest more in recipient communities' ‘techno-social reproduction’, i.e., their collective autonomy and existing mutual aid, which can be enabled or constrained by technology.

Drawing upon fieldwork, interviews and grey literature, this article focuses on the experiences of Kenya's ‘double registered’: citizens registered as refugees. Due to policy decisions dating back to at least 2000, tens of thousands of Kenyan citizens, whose biometrics were captured in government and UNHCR refugee databases, have struggled to obtain national IDs. Stuck in legal limbo, recognised neither as fully refugees nor as citizens, they have faced many problems accessing public and private services. This article, which traces how humanitarian data came to be repurposed for citizenship determination, makes two major interventions. Firstly, it suggests that more attention needs to be paid to bordering practices within humanitarian spaces, including the digitised mechanisms aimed at keeping people out of refugee camps. Secondly, building upon recent insights by scholars of media and technology, it argues that the harms associated with biometric systems must be situated within a broader understanding of how sovereignty functions in humanitarian spaces. Looking at the data governance problems that stem from spaces of fragmented sovereignty, I show that biometric initiatives in the refugee sector are not so easily divorced from the gatekeeping mechanisms of the nation-state—including its exclusionary desire to separate ‘citizens’ from ‘foreigners.’

Technological interventions in aid are both complex and deeply ambiguous. Nonetheless, many contemporary controversies surrounding humanitarian data reflect underlying tensions that stem from competing claims over sovereignty. That is, where disputes arise in humanitarian contexts following the unauthorized access to data by a third party, the unconsented sharing of humanitarian data, or the imposition of interoperability requirements on the technical systems of humanitarian agencies, these disputes regularly exhibit deeper concerns about power and authority that go beyond traditional privacy or data protection claims. This article explains the interpretive value of such a sovereignty lens on humanitarian data. To do so, it first provides an overview of how humanitarian data is shared by different actors involved in aid. Then it unpacks the meanings of sovereignty in the humanitarian domain while highlighting the emergence of “pseudo-sovereigns,” that is, actors who assert sovereignty over data in ways that challenge established norms and practices. The analysis reinterprets recent controversies surrounding the collection and sharing of biometrics, namely concerning the Rohingya in Bangladesh, Houthi in Yemen, “double registered” people in Kenya, and as part of the humanitarian response in Ukraine, through a sovereignty lens to demonstrate the utility of this perspective on humanitarian data. To better account for the complexities of power, I encourage scholars to center sovereignty considerations in their analyses of surveillance and privacy in humanitarian innovation.

The Labour Party seems intent on repeating past mistakes – from Blair-era failed experiments to the Windrush scandal – in their approach to digitising migration controls and pushing forward a mandatory national identity scheme.

Our research with humanitarians navigating the current funding crisis asks: what should the future of humanitarian data management look like?

When humanitarians adopt low earth orbit connectivity (like Musk's Starlink) for critical aid activities, what are the risks?

This report provides a comprehensive analysis of migration and refugee management in Kenya, locating current efforts to digitize migrant identification in historical context. Identity innovation needs to be contextualized within the everyday legal and bureaucratic practices that shape social, economic, and political access. Semi-structured interviews with key stakeholders and focus group discussion with migrants, asylum seekers, and refugees reveal the various challenges in and obstacles to obtaining identification within Kenya. Identification is key to integration, and addressing issues of access to ID is essential. The report also provides recommendations for donors, development actors, the Kenyan government, UNHCR, and civil society groups to improve access to ID for marginalized groups.

Identification for asylum seekers and migrants in Europe is a complex and shifting landscape. There are discrepancies between national and European-level rules and regulations, all of which are subject to change. Much of the information regarding identification requirements is also siloed in different government and public databases and, in some cases, inaccessible. This study describes how migrants experience identification systems as they travel to and throughout Europe and the various challenges they may face when trying to acquire identification or to identify themselves. In doing so, it identifies key points of friction and provides insights into the intersection of digital identity management, migration policy, and human rights in the European context. Through scenarios that follow migrants and asylum seekers from diverse countries of origin, this study illustrates specific aspects of the procedural and identification requirements many face when migrating into the European Union.

If the EU's new digital identity wallet is to be an enabler of cross-border movement, and supporter of the migration and expertise that Europe needs, which challenges need to be addressed?

Tech pilots aren’t just designed to help people: regardless of what they achieve, they are valuable products for aid industry actors to promote.

When aid professionals adopt high tech pilot projects, ignorance, blind faith, misplaced trust, and authentic expertise all come into play. Based on ethnographic research in Jordan, I examine how a refugee aid organisation produces and applies a blockchain pilot. Innovative pilots help international aid organisations attract and maintain their funding sources and reputations. I argue that The Blockchain Pilot is ‘conjured’ as a product to be promoted to a marketplace of aid donors. ‘Conjurings’ are the spectacles and magical appearances that draw an audience of investors. Ethnographic research suggests that conjurings drive capitalist markets. Rather than just requiring knowledge and expertise, I argue that conjurings entail key forms of ignorance: (i) confusion, (ii) illusion, (iii) disappearance, and (iv) misdirection. This ignorance is both strategic and inadvertent. Ignorance, just like knowledge, is shaped by hierarchical power relations. The organisation’s experimental adoption of a blockchain database system benefits some stakeholders (innovators, private partners) more than others (local aid workers and refugees). The conjuring of the pilot is what justifies the adoption of blockchain, even though a simple database would have sufficed.

The government may be trying to extract money from Kenya’s population and pay for its costly new digital identity project (Maisha Namba) by hiking fees. But amidst a cost-of-living crisis, these increased costs are not going down well with Kenya’s youth.
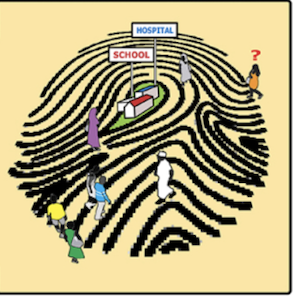
A cartoon exploring how clashes between refugee biometric databases and national ID systems affect real people like Ahmed.

Amnesty International: This is an introduction to the pervasive and rapid deployment of digital technologies in asylum and migration management systems across the globe including the United States, United Kingdom and the European Union. Defending the rights of refugees and migrants in the digital age, highlights some of the key digital technology developments in asylum and migration management systems, in particular systems that process large quantities of data, and the human rights issues arising from their use. This introductory briefing aims to build our collective understanding of these emerging technologies and hopes to add to wider advocacy efforts to stem their harmful effects.

The European Digital Identity Wallet (EUDI Wallet) is an ambitious new digital identification infrastructure proposed by the European Commission. At a basic level, a digital wallet is an electronic method of storing, managing, and exchanging money and/or identity credentials, often through the use of mobile devices. The digital wallet model is important because it reconfigures institutional arrangements, privacy protections, patterns of authority, and the very landscape of trust surrounding digital identity and payment. The main aim of the EUDI Wallet is to provide European citizens, residents, and businesses with a means to access public and private services across the EU, making it easier for them to identify, verify, and authenticate themselves in member states other than their own. Our latest report provides an accessible overview of the EUDI Wallet and interrogates why this matters and to whom. Read the report and access the policy recommendations.

DPI is neither good, nor bad but never neutral—governance is the key to achieving the goals of DPI and Digital Transformation

It is increasingly challenging for policymakers and other stakeholders to appreciate the growing complexity of the digital identity ecosystem, the technologies involved, and the broad implications of their deployment. This article seeks to help clarify these current debates and controversies by highlighting some of the technological transformations that are underway in the sector. We trace the ongoing transitions from "Big ID" systems to self-sovereign identity (SSI) approaches and digital wallets to the recent emergence of super apps, analyzing the different geographies of these systems and their impacts on exclusion and power relations. We argue that all technologies are political, and digital identity technologies especially so. Despite recent moves towards decentralization couched in the rhetoric of individual empowerment, most systems continue to exhibit features of centralization and tend to reinforce existing institutional arrangements.

Private sector actors have long been involved in surveillance. This extends to surveillance undertaken in crisis contexts and conflict situations, where humanitarian needs commonly arise. Prior research has problematized the surveillance-industrial complex’s involvement in aid initiatives and humanitarian interventions, but new dynamics are creating novel dilemmas. This contribution to a dialogue on surveillance in contemporary conflict discusses how surveillance firms are exploiting humanitarian crises as a means to aidwash their technologies and services. In this context, aidwashing practices involve the use of corporate social responsibility initiatives and forms of public-private partnership with aid actors to burnish surveillance firms’ reputations and distract the public from corporate misbehavior, ethical misdeeds, and dubious data practices. In this piece, I draw on two recent cases—a partnership to develop advanced data analytics for the optimization of humanitarian food assistance and the donation of facial recognition services in an ongoing armed conflict—to interrogate the surveillance industry’s public relations activities in humanitarian emergencies and conflict situations and reflect on the inner workings of—and resistance to—aidwashing.

Blockchain-based digital wallets were meant to empower refugee women. The reality was more complicated.

Debates are ongoing on the limits of – and possibilities for – sovereignty in the digital era. While most observers spotlight the implications of the Internet, cryptocurrencies, artificial intelligence/machine learning and advanced data analytics for the sovereignty of nation states, a critical yet under examined question concerns what digital innovations mean for authority, power and control in the humanitarian sphere in which different rules, values and expectations are thought to apply. This forum brings together practitioners and scholars to explore both conceptually and empirically how digitisation and datafication in aid are (re)shaping notions of sovereign power in humanitarian space. The forum’s contributors challenge established understandings of sovereignty in new forms of digital humanitarian action. Among other focus areas, the forum draws attention to how cyber dependencies threaten international humanitarian organisations’ purported digital sovereignty. It also contests the potential of technologies like blockchain to revolutionise notions of sovereignty in humanitarian assistance and hypothesises about the ineluctable parasitic qualities of humanitarian technology. The forum concludes by proposing that digital technologies deployed in migration contexts might be understood as ‘sovereignty experiments’. We invite readers from scholarly, policy and practitioner communities alike to engage closely with these critical perspectives on digitisation and sovereignty in humanitarian space.

Blockchain is often viewed as a revolutionary, borderless digital infrastructure that revolutionises humanitarian payments by circumventing the fragilities of would-be sovereign, national financial systems in the 'Global South'. To what extent is this vision accurate?

Aid organizations, governments, technology companies, and others have begun testing digital wallet projects that either target, or incidentally affect, migrants and refugees along with mainstream citizens. In cross-border and migration contexts, digital wallets promise to have wide ranging implications for global governance, especially in identity management and finance. In this brief Margie Cheesman outlines use cases as well as concerns and risks when it comes to their adoption in the migration sector. The brief is part of the “Dialogue on Tech and Migration, DoT.Mig.” paper series by the “Migration Strategy Group”, an initiative by the German Marshall Fund of the United States, the Bertelsmann Foundation, and the Robert Bosch Stiftung.
This Alan Turing Institute report summarizes the key takeaways from a workshop on researching digital identity in times of crisis, focusing on the implications of the pandemic for digital identity in aid and development. The workshop highlighted the disconnect between digital identity debates in the Global North and South, the dynamics of data-sharing and interoperability, and the need for more research on the digital identity industry. It calls for a comparative analysis of digital identity schemes across global divides, considering the political-economic structures that shape technological design. The report also emphasizes the importance of understanding the power dynamics in data governance and the role of private sector actors in the aid sector.

Digital identity raises concerns around privacy, power, and surveillance in global governance. Can an emergent family of 'decentralised' solutions make all the difference?

Identification technologies like biometrics have long been associated with securitisation, coercion and surveillance but have also, in recent years, become constitutive of a politics of empowerment, particularly in contexts of international aid. Aid organisations tend to see digital identification technologies as tools of recognition and inclusion rather than oppressive forms of monitoring, tracking and top-down control. In addition, practices that many critical scholars describe as aiding surveillance are often experienced differently by humanitarian subjects. This commentary examines the fraught questions this raises for scholars of international aid, surveillance studies and critical data studies. We put forward a research agenda that tackles head-on how critical theories of data and society can better account for the ambivalent dynamics of ‘power over’ and ‘power to’ that digital aid interventions instantiate.
The political drive to develop digital identity systems, in particular in the Global South with financial and technical support provided by international development actors, is accelerating during the COVID-19 pandemic. There are different reasons for this redoubling of attention to digitizing identities. These include an increased emphasis on digital social protection during the pandemic and the emergence of proposals for digital vaccination/immunity certificates to facilitate the reopening of societies and restoration of economies, which it is argued would need to be supported by robust digital identity infrastructures. Without evaluating the merits of claims about the capacity of digital identity systems to address the various challenges posed by COVID-19, in this paper I instead make a theoretical observation before raising a policy concern. First, I draw attention to the rise of India’s Aadhaar as an exemplar of developmental digital identity, which has intensified during the pandemic, and what this might mean for concepts of surveillance. I then conclude with a call to the development community to take more seriously investments in data protection regulatory capacity in countries where they are supporting digital identity projects.

This paper critically examines the implications of ‘self-sovereign identity’ (SSI) for border politics and migration management. SSI refers to user-controlled, decentralised forms of digital identification. Closely linked with the distributed ledger technology blockchain, SSI is presented by advocates as a tool to empower marginalised groups, including refugees. Among other benefits, some claim that SSI removes the need for powerful, centralised institutional structures by giving individuals control and ownership of their identity information. However, through ethnographic research in an international aid organisation, I find that SSI is an embryonic technology with indeterminate properties and benefits. I identify a series of competing logics in the debates around SSI’s emancipatory potential, which relate to four issues: (i) the neutrality of the technology, (ii) the capacities of refugees, (iii) global governance and the nation state, and (iv) new economic models for digital identity. SSI is simultaneously the potential enabler of new modes of empowerment, autonomy and data security for refugees and a means of maintaining and extending bureaucratic and commercial power. I situate SSI in a genealogy of systems of identity control and argue that, in practice, it is likely to feed into the powers of corporations and states over refugee populations.

Dr Keren Weitzberg in the London Review of Books: 'Biometrics may close the gap between an ID and its holder, but it opens a gulf between streamlined bureaucracies and people’s messy lives, their constrained choices, their survival strategies, their hopes for a better future, none of which can be captured on a digital scanner or encoded into a database.'

This paper examines refugees' experiences with and perspectives on the digital identity systems used by humanitarian organizations to collect, manage, and share their personal data. Through a qualitative study with 198 refugees in Lebanon, Jordan, and Uganda, we show how existing humanitarian identity systems present numerous challenges for refugees. For example, we find that refugees have little to no knowledge of the institutional systems and processes through which their personal data are managed and used. In addition, refugees are typically not able to exercise agency with regard to data that are collected about them (e.g. given choices about the data collected). At the same time, we show how refugees make active efforts to negotiate the various identities available to them, consciously weighing the benefits and constraints associated with different statuses to maximize their access to services, eligibility for employment, and spatial mobility. We engage with Taylor's lens of data justice to make sense of our findings and conclude by highlighting the potential of feminist science and technology study frameworks to further develop theories of data justice that can support analysis of identification systems that serve the interests of the most vulnerable.